How to Implement Forensic Watermarking
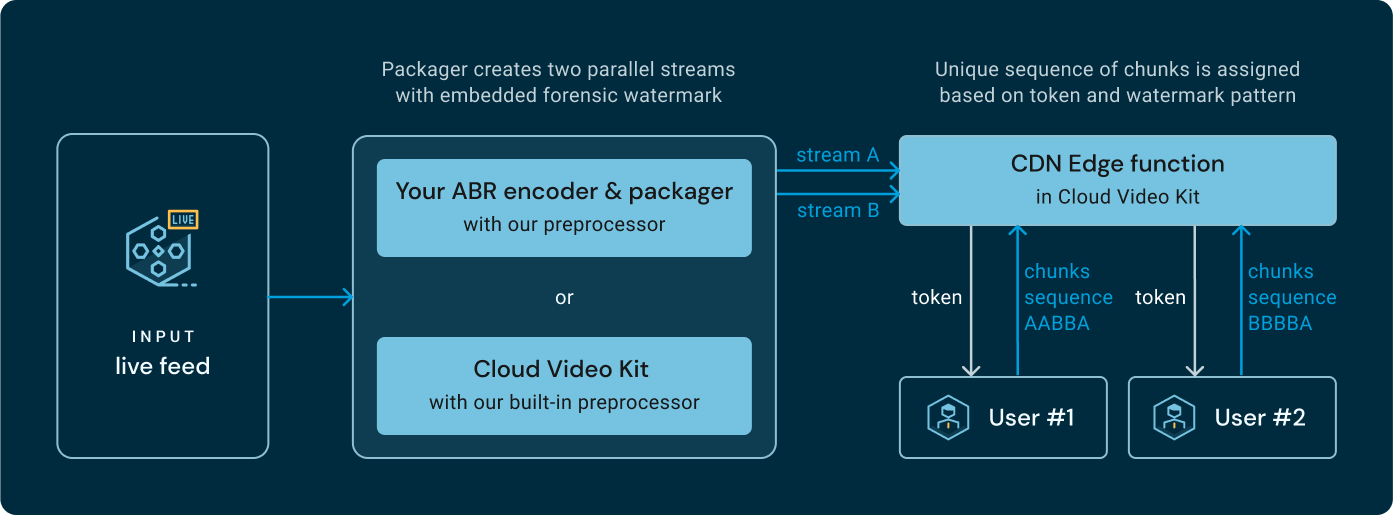
This guide provides a complete, step-by-step walkthrough for integrating Cloud Video Kit's forensic watermarking into your video player. Forensic watermarking is a powerful security feature that helps identify the source of unauthorized content distribution. If a watermarked video is leaked, the pattern can be extracted and traced back to the specific user and session, enabling you to take appropriate action.
Understanding Forensic Watermarking
Forensic watermarking embeds unique, invisible information into each video playback session. This allows you to trace the source of unauthorized copies and deter piracy, while remaining invisible to viewers. Unlike visible watermarks, forensic watermarks are designed to be resilient to various forms of content manipulation and are not easily removed without degrading the content.
Prerequisites
To successfully implement forensic watermarking, you will need the following:
- Access to the Watermarking feature. You may need to contact Cloud Video Kit to enable this feature for your account and channel.
- Endpoints to a channel with Watermarking enabled from your Cloud Video Kit console. These include your content manifest URLs.
- JWT Signing Key for Watermarking and/or DRM.
1) Obtain Endpoints for video player
Log in to the Cloud Video Kit Console and navigate to your channel. Then switch to the "Configuration" tab and copy the playback endpoints for your content.
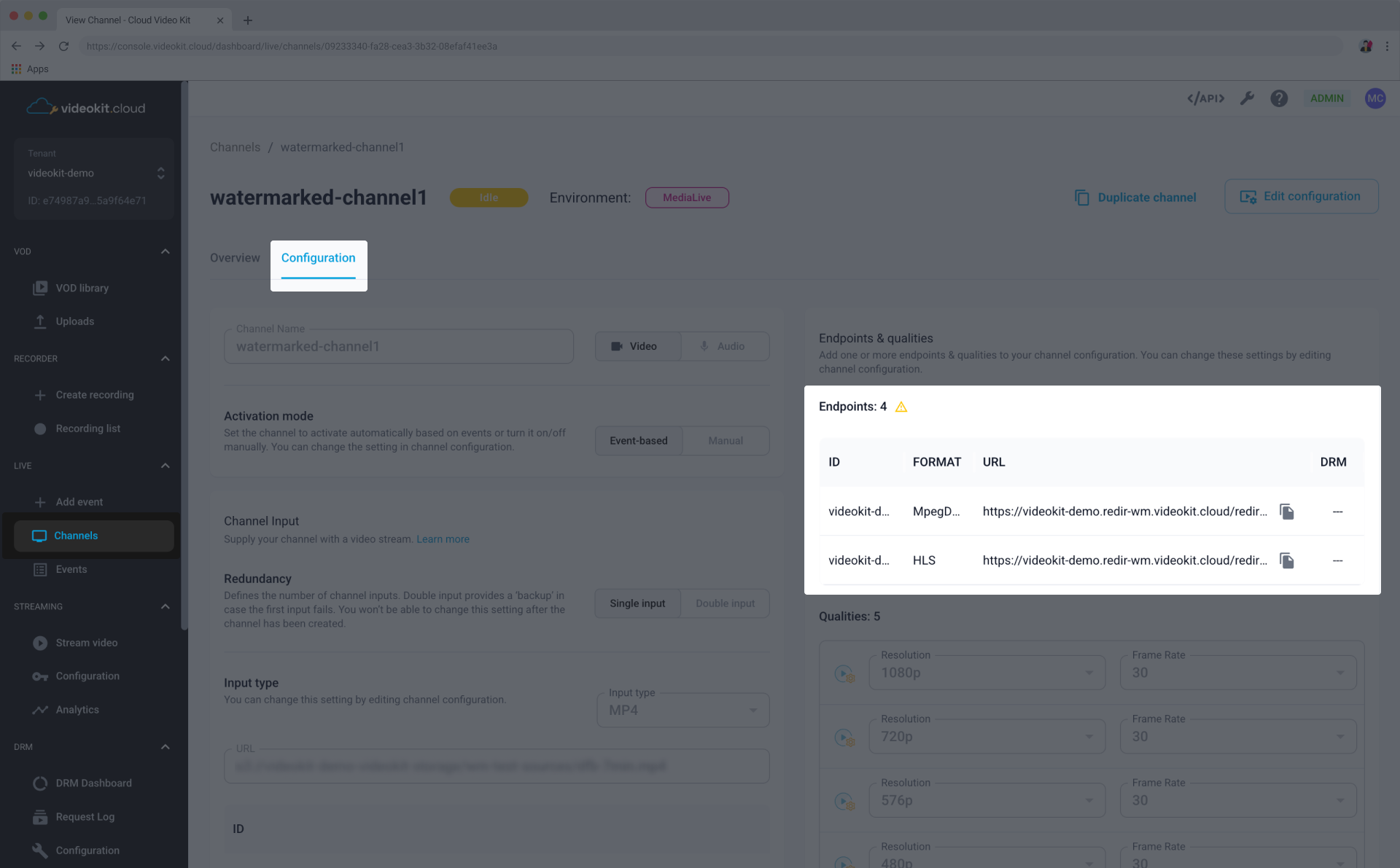
These URLs are the base for your playback. However, they are not yet complete for watermarked playback. To enable watermarking and DRM, you must append a ?usertoken=USER_TOKEN query parameter to these endpoints, where USER_TOKEN will be a dynamically generated JWT.
2) Generate the UserToken
The UserToken is the core of the watermarking implementation. It's a JWT with an HS256 signature that authorizes a user's session to access DRM-protected and watermarked content. You must generate this token on your backend for each individual user session.
The token's payload must include specific claims to enable watermarking.
JWT Payload Claims
| Claim | Required | Type | Notes |
|---|---|---|---|
exp | Yes | integer | Expiration time for the token, as a Unix timestamp. |
kid | Yes | Array of strings | An array of key identifiers. Use ["*"] to allow all keys. |
duration | Yes | integer | The duration, in seconds, for which the DRM license will be valid. |
userid | Yes (for Watermarking) | string | A unique identifier for the end-user (e.g., user_12345). |
sid | Yes (for Watermarking) | string | A unique session identifier, in GUID format (e.g., 24209ed3-50bd-4f63-bf37-7d075e8d62ac). |
Below are examples of JWT payloads. The first is for standard DRM, while the second includes the required fields for forensic watermarking.
{
"exp": 1917498278,
"kid": ["*"],
"duration": 86400
}
{
"exp": 1917498278,
"kid": ["*"],
"duration": 86400,
"userid": "user_12345",
"sid": "24209ed3-50bd-4f63-bf37-7d075e8d62ac"
}
After creating the JSON payload, sign it with your JWT Signing Key using the HS256 algorithm. The result is the complete UserToken.
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE5MTc0OTgyNzgsImtpZCI6WyIqIl0sImR1cmF0aW9uIjo4NjQwMCwidXNlcmlkIjoidXNlcl8xMjM0NSIsInNpZCI6IjI0MjA5ZWQzLTUwYmQtNGY2My1iZjM3LTdkMDc1ZThkNjJhYyJ9.some_generated_signature_hash
Read more about generating JWTs in our Cloud DRM documentation.
3) Attach UserToken to Endpoint
Append the generated UserToken as a query parameter to your manifest or license endpoint:
https://your-tenant.cdn.videokit.cloud/path/to/manifest.mpd?usertoken=YOUR_JWT_TOKEN
Pass this URL to your video player.
4) Integrate with Your Player and Verify
Use the newly constructed URL as the source for your DRM-capable video player. The player will now request the video manifest using the UserToken, which allows our system to apply the forensic watermark before playback begins.
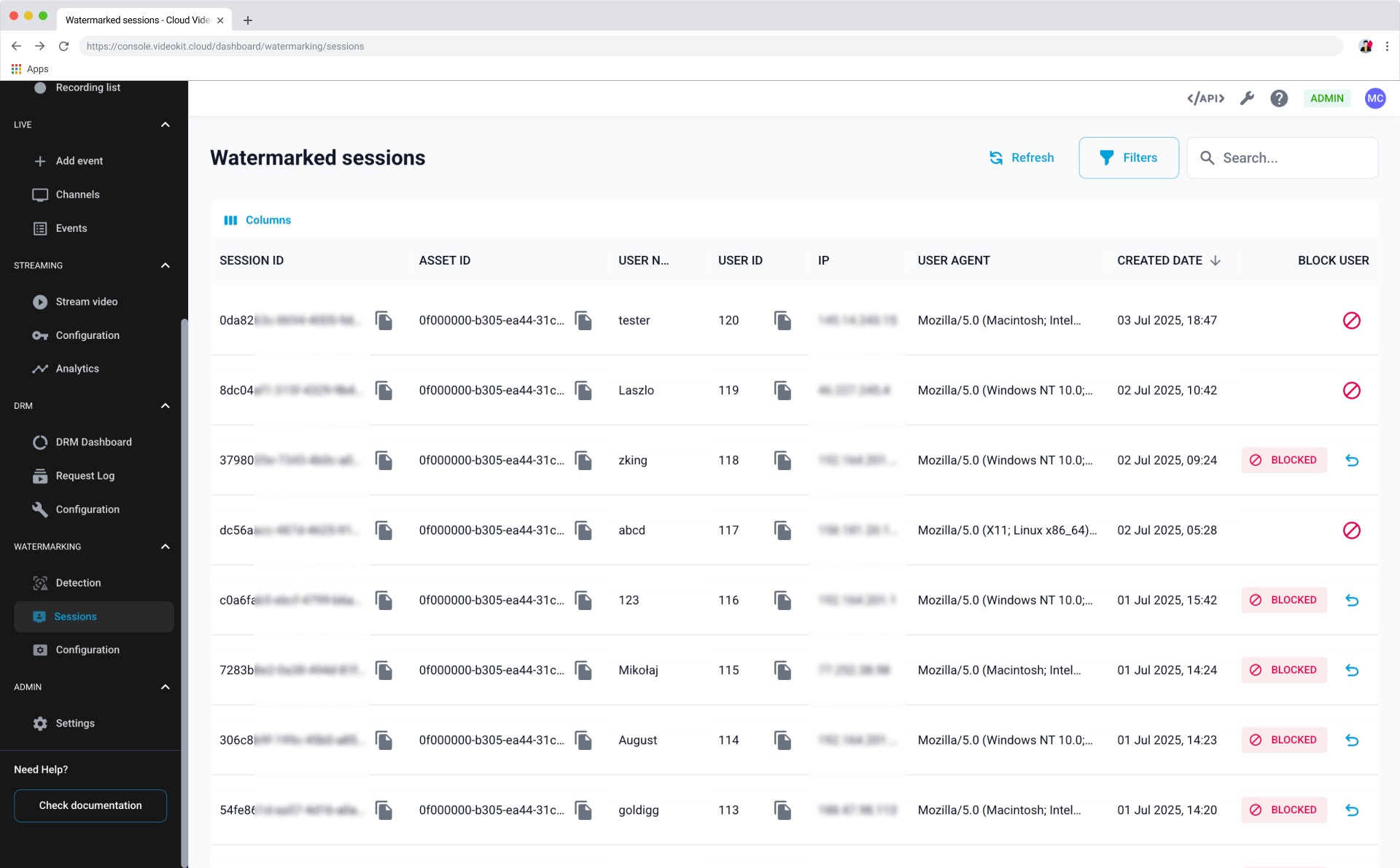
To verify that the implementation is working correctly, play a video and then check the "Watermarked sessions" section in your CVK console. Your new viewing session should appear on the list.
If you are already using our Cloud DRM service, you can use your existing JWT generation logic. Just add the userid and sid claims to the token payload and append the token to your manifest URL as described above.
Handling Issues
This section addresses common issues that can occur during implementation.
- Invalid Token Signature: This error usually means the JWT was not signed correctly or the wrong JWT Signing Key was used. Ensure you are using the HS256 algorithm and the correct JWT Signing Key from the CVK console.
- Access Denied / 403 Forbidden Error: This can happen if the
UserTokenhas expired. Check that theexp(expiration) claim is set to a future timestamp. It can also indicate an issue with thekidclaim. - Incorrect
sidFormat: Ensure thesidis a GUID string, to guarantee uniqueness for every single viewing session.